Bond / Link Aggregation
The bonding interface provides a method for aggregating multiple network interfaces into a single logical “bonded” interface, or LAG, or ether-channel, or port-channel. The behavior of the bonded interfaces depends upon the mode; generally speaking, modes provide either hot standby or load balancing services. Additionally, link integrity monitoring may be performed.
Configuration
Common interface configuration
Configure interface <interface> with one or more interface addresses.
address can be specified multiple times as IPv4 and/or IPv6 address, e.g. 192.0.2.1/24 and/or 2001:db8::1/64
dhcp interface address is received by DHCP from a DHCP server on this segment.
dhcpv6 interface address is received by DHCPv6 from a DHCPv6 server on this segment.
Note
When using DHCP to retrieve IPv4 address and if local customizations are needed, they should be possible using the enter and exit hooks provided. The hook dirs are:
/config/scripts/dhcp-client/pre-hooks.d//config/scripts/dhcp-client/post-hooks.d/
Example:
set interfaces bonding bond0 address 192.0.2.1/24
set interfaces bonding bond0 address 2001:db8::1/64
set interfaces bonding bond0 address dhcp
set interfaces bonding bond0 address dhcpv6
Set a human readable, descriptive alias for this connection. Alias is used by
e.g. the show interfaces command or SNMP based monitoring tools.
Example:
set interfaces bonding bond0 description 'This is an awesome interface running on VyOS'
Disable given <interface>. It will be placed in administratively down
(A/D) state.
Example:
set interfaces bonding bond0 disable
Ethernet flow control is a mechanism for temporarily stopping the transmission of data on Ethernet family computer networks. The goal of this mechanism is to ensure zero packet loss in the presence of network congestion.
The first flow control mechanism, the pause frame, was defined by the IEEE 802.3x standard.
A sending station (computer or network switch) may be transmitting data faster than the other end of the link can accept it. Using flow control, the receiving station can signal the sender requesting suspension of transmissions until the receiver catches up.
Use this command to disable the generation of Ethernet flow control (pause frames).
Example:
set interfaces bonding bond0 disable-flow-control
Use this command to direct an interface to not detect any physical state changes on a link, for example, when the cable is unplugged.
Default is to detects physical link state changes.
Example:
set interfaces bonding bond0 disable-link-detect
Configure user defined MAC address on given <interface>.
Example:
set interfaces bonding bond0 mac '00:01:02:03:04:05'
Configure MTU on given <interface>. It is the size (in bytes) of the largest ethernet frame sent on this link.
Example:
set interfaces bonding bond0 mtu 1600
As Internet wide PMTU discovery rarely works, we sometimes need to clamp our TCP MSS value to a specific value. This is a field in the TCP options part of a SYN packet. By setting the MSS value, you are telling the remote side unequivocally ‘do not try to send me packets bigger than this value’.
Note
This command was introduced in VyOS 1.4 - it was previously called:
set firewall options interface <name> adjust-mss <value>
Hint
MSS value = MTU - 20 (IP header) - 20 (TCP header), resulting in 1452 bytes on a 1492 byte MTU.
Instead of a numerical MSS value clamp-mss-to-pmtu can be used to automatically set the proper value.
Once a neighbor has been found, the entry is considered to be valid for at least for this specific time. An entry’s validity will be extended if it receives positive feedback from higher level protocols.
This defaults to 30 seconds.
Example:
set interfaces bonding bond0 ip arp-cache-timeout 180
If set the kernel can respond to arp requests with addresses from other interfaces. This may seem wrong but it usually makes sense, because it increases the chance of successful communication. IP addresses are owned by the complete host on Linux, not by particular interfaces. Only for more complex setups like load-balancing, does this behaviour cause problems.
If not set (default) allows you to have multiple network interfaces on the same subnet, and have the ARPs for each interface be answered based on whether or not the kernel would route a packet from the ARP’d IP out that interface (therefore you must use source based routing for this to work).
In other words it allows control of which cards (usually 1) will respond to an arp request.
Example:
set interfaces bonding bond0 ip disable-arp-filter
Configure interface-specific Host/Router behaviour. If set, the interface will switch to host mode and IPv6 forwarding will be disabled on this interface.
set interfaces bonding bond0 ip disable-forwarding
Define different modes for IP directed broadcast forwarding as described in RFC 1812 and RFC 2644.
If configured, incoming IP directed broadcast packets on this interface will be forwarded.
If this option is unset (default), incoming IP directed broadcast packets will not be forwarded.
set interfaces bonding bond0 ip enable-directed-broadcast
Define behavior for gratuitous ARP frames who’s IP is not already present in the ARP table. If configured create new entries in the ARP table.
Both replies and requests type gratuitous arp will trigger the ARP table to be updated, if this setting is on.
If the ARP table already contains the IP address of the gratuitous arp frame, the arp table will be updated regardless if this setting is on or off.
set interfaces bonding bond0 ip enable-arp-accept
Define different restriction levels for announcing the local source IP address from IP packets in ARP requests sent on interface.
Use any local address, configured on any interface if this is not set.
If configured, try to avoid local addresses that are not in the target’s subnet for this interface. This mode is useful when target hosts reachable via this interface require the source IP address in ARP requests to be part of their logical network configured on the receiving interface. When we generate the request we will check all our subnets that include the target IP and will preserve the source address if it is from such subnet. If there is no such subnet we select source address according to the rules for level 2.
set interfaces bonding bond0 ip enable-arp-announce
Define different modes for sending replies in response to received ARP requests that resolve local target IP addresses:
If configured, reply only if the target IP address is local address configured on the incoming interface.
If this option is unset (default), reply for any local target IP address, configured on any interface.
set interfaces bonding bond0 ip enable-arp-ignore
Use this command to enable proxy Address Resolution Protocol (ARP) on this interface. Proxy ARP allows an Ethernet interface to respond with its own MAC address to ARP requests for destination IP addresses on subnets attached to other interfaces on the system. Subsequent packets sent to those destination IP addresses are forwarded appropriately by the system.
Example:
set interfaces bonding bond0 ip enable-proxy-arp
Private VLAN proxy arp. Basically allow proxy arp replies back to the same interface (from which the ARP request/solicitation was received).
This is done to support (ethernet) switch features, like RFC 3069, where the individual ports are NOT allowed to communicate with each other, but they are allowed to talk to the upstream router. As described in RFC 3069, it is possible to allow these hosts to communicate through the upstream router by proxy_arp’ing.
Note
Does not need to be used together with proxy_arp.
This technology is known by different names:
In RFC 3069 it is called VLAN Aggregation
Cisco and Allied Telesyn call it Private VLAN
Hewlett-Packard call it Source-Port filtering or port-isolation
Ericsson call it MAC-Forced Forwarding (RFC Draft)
Enable policy for source validation by reversed path, as specified in RFC 3704. Current recommended practice in RFC 3704 is to enable strict mode to prevent IP spoofing from DDos attacks. If using asymmetric routing or other complicated routing, then loose mode is recommended.
strict: Each incoming packet is tested against the FIB and if the interface is not the best reverse path the packet check will fail. By default failed packets are discarded.
loose: Each incoming packet’s source address is also tested against the FIB and if the source address is not reachable via any interface the packet check will fail.
disable: No source validation
SLAAC RFC 4862. IPv6 hosts can configure themselves automatically when connected to an IPv6 network using the Neighbor Discovery Protocol via ICMPv6 router discovery messages. When first connected to a network, a host sends a link-local router solicitation multicast request for its configuration parameters; routers respond to such a request with a router advertisement packet that contains Internet Layer configuration parameters.
Note
This method automatically disables IPv6 traffic forwarding on the interface in question.
Example:
set interfaces bonding bond0 ipv6 address autoconf
EUI-64 as specified in RFC 4291 allows a host to assign iteslf a unique 64-Bit IPv6 address.
Example:
set interfaces bonding bond0 ipv6 address eui64 2001:db8:beef::/64
Do not assign a link-local IPv6 address to this interface.
Example:
set interfaces bonding bond0 ipv6 address no-default-link-local
Configure interface-specific Host/Router behaviour. If set, the interface will switch to host mode and IPv6 forwarding will be disabled on this interface.
Example:
set interfaces bonding bond0 ipv6 disable-forwarding
As Internet wide PMTU discovery rarely works, we sometimes need to clamp our TCP MSS value to a specific value. This is a field in the TCP options part of a SYN packet. By setting the MSS value, you are telling the remote side unequivocally ‘do not try to send me packets bigger than this value’.
Note
This command was introduced in VyOS 1.4 - it was previously called:
set firewall options interface <name> adjust-mss6 <value>
Hint
MSS value = MTU - 40 (IPv6 header) - 20 (TCP header), resulting in 1432 bytes on a 1492 byte MTU.
Instead of a numerical MSS value clamp-mss-to-pmtu can be used to automatically set the proper value.
Whether to accept DAD (Duplicate Address Detection).
0: Disable DAD
1: Enable DAD (default)
2: Enable DAD, and disable IPv6 operation if MAC-based duplicate link-local address has been found.
Example:
set interfaces bonding bond0 ipv6 accept-dad 2
The amount of Duplicate Address Detection probes to send.
Default: 1
Example:
set interfaces bonding bond0 ipv6 dup-addr-detect-transmits 5
Place interface in given VRF instance.
See also
There is an entire chapter about how to configure a VRF, please check this for additional information.
Example:
set interfaces bonding bond0 vrf red
DHCP(v6)
RFC 2131 states: The client MAY choose to explicitly provide the identifier through the ‘client identifier’ option. If the client supplies a ‘client identifier’, the client MUST use the same ‘client identifier’ in all subsequent messages, and the server MUST use that identifier to identify the client.
Example:
set interfaces bonding bond0 dhcp-options client-id 'foo-bar'
Instead of sending the real system hostname to the DHCP server, overwrite the host-name with this given-value.
Example:
set interfaces bonding bond0 dhcp-options host-name 'VyOS'
The vendor-class-id option can be used to request a specific class of vendor options from the server.
Example:
set interfaces bonding bond0 dhcp-options vendor-class-id 'VyOS'
Only request an address from the DHCP server but do not request a default gateway.
Example:
set interfaces bonding bond0 dhcp-options no-default-route
Set the distance for the default gateway sent by the DHCP server.
Example:
set interfaces bonding bond0 dhcp-options default-route-distance 220
Reject DHCP leases from a given address or range. This is useful when a modem gives a local IP when first starting.
address can be specified multiple times, e.g. 192.168.100.1 and/or 192.168.100.0/24
Example:
set interfaces bonding bond0 dhcp-options reject 192.168.100.0/24
The DHCP unique identifier (DUID) is used by a client to get an IP address from a DHCPv6 server. It has a 2-byte DUID type field, and a variable-length identifier field up to 128 bytes. Its actual length depends on its type. The server compares the DUID with its database and delivers configuration data (address, lease times, DNS servers, etc.) to the client.
set interfaces bonding bond0 duid '0e:00:00:01:00:01:27:71:db:f0:00:50:56:bf:c5:6d'
When no-release is specified, dhcp6c will send a release message on client exit to prevent losing an assigned address or prefix.
set interfaces bonding bond0 dhcpv6-options no-release
This statement specifies dhcp6c to only exchange informational configuration parameters with servers. A list of DNS server addresses is an example of such parameters. This statement is useful when the client does not need stateful configuration parameters such as IPv6 addresses or prefixes.
set interfaces bonding bond0 dhcpv6-options parameters-only
When rapid-commit is specified, dhcp6c will include a rapid-commit option in solicit messages and wait for an immediate reply instead of advertisements.
set interfaces bonding bond0 dhcpv6-options rapid-commit
Request only a temporary address and not form an IA_NA (Identity Association for Non-temporary Addresses) partnership.
set interfaces bonding bond0 dhcpv6-options temporary
DHCPv6 Prefix Delegation (PD)
VyOS 1.3 (equuleus) supports DHCPv6-PD (RFC 3633). DHCPv6 Prefix Delegation is supported by most ISPs who provide native IPv6 for consumers on fixed networks.
Some ISPs by default only delegate a /64 prefix. To request for a specific prefix size use this option to request for a bigger delegation for this pd <id>. This value is in the range from 32 - 64 so you could request up to a /32 prefix (if your ISP allows this) down to a /64 delegation.
The default value corresponds to 64.
To request a /56 prefix from your ISP use:
set interfaces bonding bond0 dhcpv6-options pd 0 length 56
Specify the interface address used locally on the interface where the prefix has been delegated to. ID must be a decimal integer.
It will be combined with the delegated prefix and the sla-id to form a complete interface address. The default is to use the EUI-64 address of the interface.
Example: Delegate a /64 prefix to interface eth8 which will use a local
address on this router of <prefix>::ffff, as the address 65534 will
correspond to ffff in hexadecimal notation.
set interfaces bonding bond0 dhcpv6-options pd 0 interface eth8 address 65534
Specify the identifier value of the site-level aggregator (SLA) on the interface. ID must be a decimal number greater then 0 which fits in the length of SLA IDs (see below).
Example: If ID is 1 and the client is delegated an IPv6 prefix 2001:db8:ffff::/48, dhcp6c will combine the two values into a single IPv6 prefix, 2001:db8:ffff:1::/64, and will configure the prefix on the specified interface.
set interfaces bonding bond0 dhcpv6-options pd 0 interface eth8 sla-id 1
Member Interfaces
Bond options
Specifies one of the bonding policies. The default is 802.3ad. Possible values are:
802.3ad- IEEE 802.3ad Dynamic link aggregation. Creates aggregation groups that share the same speed and duplex settings. Utilizes all slaves in the active aggregator according to the 802.3ad specification.Slave selection for outgoing traffic is done according to the transmit hash policy, which may be changed from the default simple XOR policy via the
hash-policyoption, documented below.Note
Not all transmit policies may be 802.3ad compliant, particularly in regards to the packet misordering requirements of section 43.2.4 of the 802.3ad standard.
active-backup- Active-backup policy: Only one slave in the bond is active. A different slave becomes active if, and only if, the active slave fails. The bond’s MAC address is externally visible on only one port (network adapter) to avoid confusing the switch.When a failover occurs in active-backup mode, bonding will issue one or more gratuitous ARPs on the newly active slave. One gratuitous ARP is issued for the bonding master interface and each VLAN interfaces configured above it, provided that the interface has at least one IP address configured. Gratuitous ARPs issued for VLAN interfaces are tagged with the appropriate VLAN id.
This mode provides fault tolerance. The
primaryoption, documented below, affects the behavior of this mode.
broadcast- Broadcast policy: transmits everything on all slave interfaces.This mode provides fault tolerance.
round-robin- Round-robin policy: Transmit packets in sequential order from the first available slave through the last.This mode provides load balancing and fault tolerance.
transmit-load-balance- Adaptive transmit load balancing: channel bonding that does not require any special switch support.Incoming traffic is received by the current slave. If the receiving slave fails, another slave takes over the MAC address of the failed receiving slave.
adaptive-load-balance- Adaptive load balancing: includes transmit-load-balance plus receive load balancing for IPV4 traffic, and does not require any special switch support. The receive load balancing is achieved by ARP negotiation. The bonding driver intercepts the ARP Replies sent by the local system on their way out and overwrites the source hardware address with the unique hardware address of one of the slaves in the bond such that different peers use different hardware addresses for the server.Receive traffic from connections created by the server is also balanced. When the local system sends an ARP Request the bonding driver copies and saves the peer’s IP information from the ARP packet. When the ARP Reply arrives from the peer, its hardware address is retrieved and the bonding driver initiates an ARP reply to this peer assigning it to one of the slaves in the bond. A problematic outcome of using ARP negotiation for balancing is that each time that an ARP request is broadcast it uses the hardware address of the bond. Hence, peers learn the hardware address of the bond and the balancing of receive traffic collapses to the current slave. This is handled by sending updates (ARP Replies) to all the peers with their individually assigned hardware address such that the traffic is redistributed. Receive traffic is also redistributed when a new slave is added to the bond and when an inactive slave is re-activated. The receive load is distributed sequentially (round robin) among the group of highest speed slaves in the bond.
When a link is reconnected or a new slave joins the bond the receive traffic is redistributed among all active slaves in the bond by initiating ARP Replies with the selected MAC address to each of the clients. The updelay parameter (detailed below) must be set to a value equal or greater than the switch’s forwarding delay so that the ARP Replies sent to the peers will not be blocked by the switch.
xor-hash- XOR policy: Transmit based on the selected transmit hash policy. The default policy is a simple [(source MAC address XOR’d with destination MAC address XOR packet type ID) modulo slave count]. Alternate transmit policies may be selected via thehash-policyoption, described below.This mode provides load balancing and fault tolerance.
Specifies the minimum number of links that must be active before asserting carrier. It is similar to the Cisco EtherChannel min-links feature. This allows setting the minimum number of member ports that must be up (link-up state) before marking the bond device as up (carrier on). This is useful for situations where higher level services such as clustering want to ensure a minimum number of low bandwidth links are active before switchover.
This option only affects 802.3ad mode.
The default value is 0. This will cause the carrier to be asserted (for 802.3ad mode) whenever there is an active aggregator, regardless of the number of available links in that aggregator.
Note
Because an aggregator cannot be active without at least one available link, setting this option to 0 or to 1 has the exact same effect.
Option specifying the rate in which we’ll ask our link partner to transmit LACPDU packets in 802.3ad mode.
This option only affects 802.3ad mode.
slow: Request partner to transmit LACPDUs every 30 seconds
fast: Request partner to transmit LACPDUs every 1 second
The default value is slow.
layer2 - Uses XOR of hardware MAC addresses and packet type ID field to generate the hash. The formula is
hash = source MAC XOR destination MAC XOR packet type ID slave number = hash modulo slave count
This algorithm will place all traffic to a particular network peer on the same slave.
This algorithm is 802.3ad compliant.
layer2+3 - This policy uses a combination of layer2 and layer3 protocol information to generate the hash. Uses XOR of hardware MAC addresses and IP addresses to generate the hash. The formula is:
hash = source MAC XOR destination MAC XOR packet type ID hash = hash XOR source IP XOR destination IP hash = hash XOR (hash RSHIFT 16) hash = hash XOR (hash RSHIFT 8)
And then hash is reduced modulo slave count.
If the protocol is IPv6 then the source and destination addresses are first hashed using ipv6_addr_hash.
This algorithm will place all traffic to a particular network peer on the same slave. For non-IP traffic, the formula is the same as for the layer2 transmit hash policy.
This policy is intended to provide a more balanced distribution of traffic than layer2 alone, especially in environments where a layer3 gateway device is required to reach most destinations.
This algorithm is 802.3ad compliant.
layer3+4 - This policy uses upper layer protocol information, when available, to generate the hash. This allows for traffic to a particular network peer to span multiple slaves, although a single connection will not span multiple slaves.
The formula for unfragmented TCP and UDP packets is
hash = source port, destination port (as in the header) hash = hash XOR source IP XOR destination IP hash = hash XOR (hash RSHIFT 16) hash = hash XOR (hash RSHIFT 8)
And then hash is reduced modulo slave count.
If the protocol is IPv6 then the source and destination addresses are first hashed using ipv6_addr_hash.
For fragmented TCP or UDP packets and all other IPv4 and IPv6 protocol traffic, the source and destination port information is omitted. For non-IP traffic, the formula is the same as for the layer2 transmit hash policy.
This algorithm is not fully 802.3ad compliant. A single TCP or UDP conversation containing both fragmented and unfragmented packets will see packets striped across two interfaces. This may result in out of order delivery. Most traffic types will not meet these criteria, as TCP rarely fragments traffic, and most UDP traffic is not involved in extended conversations. Other implementations of 802.3ad may or may not tolerate this noncompliance.
An <interface> specifying which slave is the primary device. The specified device will always be the active slave while it is available. Only when the primary is off-line will alternate devices be used. This is useful when one slave is preferred over another, e.g., when one slave has higher throughput than another.
The primary option is only valid for active-backup, transmit-load-balance, and adaptive-load-balance mode.
Specifies the ARP link monitoring <time> in seconds.
The ARP monitor works by periodically checking the slave devices to determine
whether they have sent or received traffic recently (the precise criteria
depends upon the bonding mode, and the state of the slave). Regular traffic
is generated via ARP probes issued for the addresses specified by the
arp-monitor target option.
If ARP monitoring is used in an etherchannel compatible mode (modes round-robin and xor-hash), the switch should be configured in a mode that evenly distributes packets across all links. If the switch is configured to distribute the packets in an XOR fashion, all replies from the ARP targets will be received on the same link which could cause the other team members to fail.
A value of 0 disables ARP monitoring. The default value is 0.
Specifies the IP addresses to use as ARP monitoring peers when
arp-monitor interval option is > 0. These are the targets of the
ARP request sent to determine the health of the link to the targets.
Multiple target IP addresses can be specified. At least one IP address must be given for ARP monitoring to function.
The maximum number of targets that can be specified is 16. The default value is no IP address.
VLAN
IEEE 802.1q, often referred to as Dot1q, is the networking standard that supports virtual LANs (VLANs) on an IEEE 802.3 Ethernet network. The standard defines a system of VLAN tagging for Ethernet frames and the accompanying procedures to be used by bridges and switches in handling such frames. The standard also contains provisions for a quality-of-service prioritization scheme commonly known as IEEE 802.1p and defines the Generic Attribute Registration Protocol.
Portions of the network which are VLAN-aware (i.e., IEEE 802.1q conformant) can include VLAN tags. When a frame enters the VLAN-aware portion of the network, a tag is added to represent the VLAN membership. Each frame must be distinguishable as being within exactly one VLAN. A frame in the VLAN-aware portion of the network that does not contain a VLAN tag is assumed to be flowing on the native VLAN.
The standard was developed by IEEE 802.1, a working group of the IEEE 802 standards committee, and continues to be actively revised. One of the notable revisions is 802.1Q-2014 which incorporated IEEE 802.1aq (Shortest Path Bridging) and much of the IEEE 802.1d standard.
802.1q VLAN interfaces are represented as virtual sub-interfaces in VyOS. The
term used for this is vif.
Create a new VLAN interface on interface <interface> using the VLAN number provided via <vlan-id>.
You can create multiple VLAN interfaces on a physical interface. The VLAN ID range is from 0 to 4094.
Note
Only 802.1Q-tagged packets are accepted on Ethernet vifs.
Configure interface <interface> with one or more interface addresses.
address can be specified multiple times as IPv4 and/or IPv6 address, e.g. 192.0.2.1/24 and/or 2001:db8::1/64
dhcp interface address is received by DHCP from a DHCP server on this segment.
dhcpv6 interface address is received by DHCPv6 from a DHCPv6 server on this segment.
Note
When using DHCP to retrieve IPv4 address and if local customizations are needed, they should be possible using the enter and exit hooks provided. The hook dirs are:
/config/scripts/dhcp-client/pre-hooks.d//config/scripts/dhcp-client/post-hooks.d/
Example:
set interfaces bonding bond0 vif 10 address 192.0.2.1/24
set interfaces bonding bond0 vif 10 address 2001:db8::1/64
set interfaces bonding bond0 vif 10 address dhcp
set interfaces bonding bond0 vif 10 address dhcpv6
Set a human readable, descriptive alias for this connection. Alias is used by
e.g. the show interfaces command or SNMP based monitoring tools.
Example:
set interfaces bonding bond0 vif 10 description 'This is an awesome interface running on VyOS'
Disable given <interface>. It will be placed in administratively down
(A/D) state.
Example:
set interfaces bonding bond0 vif 10 disable
Use this command to direct an interface to not detect any physical state changes on a link, for example, when the cable is unplugged.
Default is to detects physical link state changes.
Example:
set interfaces bonding bond0 vif 10 disable-link-detect
Configure user defined MAC address on given <interface>.
Example:
set interfaces bonding bond0 vif 10 mac '00:01:02:03:04:05'
Configure MTU on given <interface>. It is the size (in bytes) of the largest ethernet frame sent on this link.
Example:
set interfaces bonding bond0 vif 10 mtu 1600
As Internet wide PMTU discovery rarely works, we sometimes need to clamp our TCP MSS value to a specific value. This is a field in the TCP options part of a SYN packet. By setting the MSS value, you are telling the remote side unequivocally ‘do not try to send me packets bigger than this value’.
Note
This command was introduced in VyOS 1.4 - it was previously called:
set firewall options interface <name> adjust-mss <value>
Hint
MSS value = MTU - 20 (IP header) - 20 (TCP header), resulting in 1452 bytes on a 1492 byte MTU.
Instead of a numerical MSS value clamp-mss-to-pmtu can be used to automatically set the proper value.
Once a neighbor has been found, the entry is considered to be valid for at least for this specific time. An entry’s validity will be extended if it receives positive feedback from higher level protocols.
This defaults to 30 seconds.
Example:
set interfaces bonding bond0 vif 10 ip arp-cache-timeout 180
If set the kernel can respond to arp requests with addresses from other interfaces. This may seem wrong but it usually makes sense, because it increases the chance of successful communication. IP addresses are owned by the complete host on Linux, not by particular interfaces. Only for more complex setups like load-balancing, does this behaviour cause problems.
If not set (default) allows you to have multiple network interfaces on the same subnet, and have the ARPs for each interface be answered based on whether or not the kernel would route a packet from the ARP’d IP out that interface (therefore you must use source based routing for this to work).
In other words it allows control of which cards (usually 1) will respond to an arp request.
Example:
set interfaces bonding bond0 vif 10 ip disable-arp-filter
Configure interface-specific Host/Router behaviour. If set, the interface will switch to host mode and IPv6 forwarding will be disabled on this interface.
set interfaces bonding bond0 vif 10 ip disable-forwarding
Define different modes for IP directed broadcast forwarding as described in RFC 1812 and RFC 2644.
If configured, incoming IP directed broadcast packets on this interface will be forwarded.
If this option is unset (default), incoming IP directed broadcast packets will not be forwarded.
set interfaces bonding bond0 vif 10 ip enable-directed-broadcast
Define behavior for gratuitous ARP frames who’s IP is not already present in the ARP table. If configured create new entries in the ARP table.
Both replies and requests type gratuitous arp will trigger the ARP table to be updated, if this setting is on.
If the ARP table already contains the IP address of the gratuitous arp frame, the arp table will be updated regardless if this setting is on or off.
set interfaces bonding bond0 vif 10 ip enable-arp-accept
Define different restriction levels for announcing the local source IP address from IP packets in ARP requests sent on interface.
Use any local address, configured on any interface if this is not set.
If configured, try to avoid local addresses that are not in the target’s subnet for this interface. This mode is useful when target hosts reachable via this interface require the source IP address in ARP requests to be part of their logical network configured on the receiving interface. When we generate the request we will check all our subnets that include the target IP and will preserve the source address if it is from such subnet. If there is no such subnet we select source address according to the rules for level 2.
set interfaces bonding bond0 vif 10 ip enable-arp-announce
Define different modes for sending replies in response to received ARP requests that resolve local target IP addresses:
If configured, reply only if the target IP address is local address configured on the incoming interface.
If this option is unset (default), reply for any local target IP address, configured on any interface.
set interfaces bonding bond0 vif 10 ip enable-arp-ignore
Use this command to enable proxy Address Resolution Protocol (ARP) on this interface. Proxy ARP allows an Ethernet interface to respond with its own MAC address to ARP requests for destination IP addresses on subnets attached to other interfaces on the system. Subsequent packets sent to those destination IP addresses are forwarded appropriately by the system.
Example:
set interfaces bonding bond0 vif 10 ip enable-proxy-arp
Private VLAN proxy arp. Basically allow proxy arp replies back to the same interface (from which the ARP request/solicitation was received).
This is done to support (ethernet) switch features, like RFC 3069, where the individual ports are NOT allowed to communicate with each other, but they are allowed to talk to the upstream router. As described in RFC 3069, it is possible to allow these hosts to communicate through the upstream router by proxy_arp’ing.
Note
Does not need to be used together with proxy_arp.
This technology is known by different names:
In RFC 3069 it is called VLAN Aggregation
Cisco and Allied Telesyn call it Private VLAN
Hewlett-Packard call it Source-Port filtering or port-isolation
Ericsson call it MAC-Forced Forwarding (RFC Draft)
Enable policy for source validation by reversed path, as specified in RFC 3704. Current recommended practice in RFC 3704 is to enable strict mode to prevent IP spoofing from DDos attacks. If using asymmetric routing or other complicated routing, then loose mode is recommended.
strict: Each incoming packet is tested against the FIB and if the interface is not the best reverse path the packet check will fail. By default failed packets are discarded.
loose: Each incoming packet’s source address is also tested against the FIB and if the source address is not reachable via any interface the packet check will fail.
disable: No source validation
SLAAC RFC 4862. IPv6 hosts can configure themselves automatically when connected to an IPv6 network using the Neighbor Discovery Protocol via ICMPv6 router discovery messages. When first connected to a network, a host sends a link-local router solicitation multicast request for its configuration parameters; routers respond to such a request with a router advertisement packet that contains Internet Layer configuration parameters.
Note
This method automatically disables IPv6 traffic forwarding on the interface in question.
Example:
set interfaces bonding bond0 vif 10 ipv6 address autoconf
EUI-64 as specified in RFC 4291 allows a host to assign iteslf a unique 64-Bit IPv6 address.
Example:
set interfaces bonding bond0 vif 10 ipv6 address eui64 2001:db8:beef::/64
Do not assign a link-local IPv6 address to this interface.
Example:
set interfaces bonding bond0 vif 10 ipv6 address no-default-link-local
Configure interface-specific Host/Router behaviour. If set, the interface will switch to host mode and IPv6 forwarding will be disabled on this interface.
Example:
set interfaces bonding bond0 vif 10 ipv6 disable-forwarding
As Internet wide PMTU discovery rarely works, we sometimes need to clamp our TCP MSS value to a specific value. This is a field in the TCP options part of a SYN packet. By setting the MSS value, you are telling the remote side unequivocally ‘do not try to send me packets bigger than this value’.
Note
This command was introduced in VyOS 1.4 - it was previously called:
set firewall options interface <name> adjust-mss6 <value>
Hint
MSS value = MTU - 40 (IPv6 header) - 20 (TCP header), resulting in 1432 bytes on a 1492 byte MTU.
Instead of a numerical MSS value clamp-mss-to-pmtu can be used to automatically set the proper value.
Whether to accept DAD (Duplicate Address Detection).
0: Disable DAD
1: Enable DAD (default)
2: Enable DAD, and disable IPv6 operation if MAC-based duplicate link-local address has been found.
Example:
set interfaces bonding bond0 vif 10 ipv6 accept-dad 2
The amount of Duplicate Address Detection probes to send.
Default: 1
Example:
set interfaces bonding bond0 vif 10 ipv6 dup-addr-detect-transmits 5
Place interface in given VRF instance.
See also
There is an entire chapter about how to configure a VRF, please check this for additional information.
Example:
set interfaces bonding bond0 vif 10 vrf red
DHCP(v6)
RFC 2131 states: The client MAY choose to explicitly provide the identifier through the ‘client identifier’ option. If the client supplies a ‘client identifier’, the client MUST use the same ‘client identifier’ in all subsequent messages, and the server MUST use that identifier to identify the client.
Example:
set interfaces bonding bond0 vif 10 dhcp-options client-id 'foo-bar'
Instead of sending the real system hostname to the DHCP server, overwrite the host-name with this given-value.
Example:
set interfaces bonding bond0 vif 10 dhcp-options host-name 'VyOS'
The vendor-class-id option can be used to request a specific class of vendor options from the server.
Example:
set interfaces bonding bond0 vif 10 dhcp-options vendor-class-id 'VyOS'
Only request an address from the DHCP server but do not request a default gateway.
Example:
set interfaces bonding bond0 vif 10 dhcp-options no-default-route
Set the distance for the default gateway sent by the DHCP server.
Example:
set interfaces bonding bond0 vif 10 dhcp-options default-route-distance 220
Reject DHCP leases from a given address or range. This is useful when a modem gives a local IP when first starting.
address can be specified multiple times, e.g. 192.168.100.1 and/or 192.168.100.0/24
Example:
set interfaces bonding bond0 vif 10 dhcp-options reject 192.168.100.0/24
The DHCP unique identifier (DUID) is used by a client to get an IP address from a DHCPv6 server. It has a 2-byte DUID type field, and a variable-length identifier field up to 128 bytes. Its actual length depends on its type. The server compares the DUID with its database and delivers configuration data (address, lease times, DNS servers, etc.) to the client.
set interfaces bonding bond0 vif 10 duid '0e:00:00:01:00:01:27:71:db:f0:00:50:56:bf:c5:6d'
When no-release is specified, dhcp6c will send a release message on client exit to prevent losing an assigned address or prefix.
set interfaces bonding bond0 vif 10 dhcpv6-options no-release
This statement specifies dhcp6c to only exchange informational configuration parameters with servers. A list of DNS server addresses is an example of such parameters. This statement is useful when the client does not need stateful configuration parameters such as IPv6 addresses or prefixes.
set interfaces bonding bond0 vif 10 dhcpv6-options parameters-only
When rapid-commit is specified, dhcp6c will include a rapid-commit option in solicit messages and wait for an immediate reply instead of advertisements.
set interfaces bonding bond0 vif 10 dhcpv6-options rapid-commit
Request only a temporary address and not form an IA_NA (Identity Association for Non-temporary Addresses) partnership.
set interfaces bonding bond0 vif 10 dhcpv6-options temporary
DHCPv6 Prefix Delegation (PD)
VyOS 1.3 (equuleus) supports DHCPv6-PD (RFC 3633). DHCPv6 Prefix Delegation is supported by most ISPs who provide native IPv6 for consumers on fixed networks.
Some ISPs by default only delegate a /64 prefix. To request for a specific prefix size use this option to request for a bigger delegation for this pd <id>. This value is in the range from 32 - 64 so you could request up to a /32 prefix (if your ISP allows this) down to a /64 delegation.
The default value corresponds to 64.
To request a /56 prefix from your ISP use:
set interfaces bonding bond0 vif 10 dhcpv6-options pd 0 length 56
Specify the interface address used locally on the interface where the prefix has been delegated to. ID must be a decimal integer.
It will be combined with the delegated prefix and the sla-id to form a complete interface address. The default is to use the EUI-64 address of the interface.
Example: Delegate a /64 prefix to interface eth8 which will use a local
address on this router of <prefix>::ffff, as the address 65534 will
correspond to ffff in hexadecimal notation.
set interfaces bonding bond0 vif 10 dhcpv6-options pd 0 interface eth8 address 65534
Specify the identifier value of the site-level aggregator (SLA) on the interface. ID must be a decimal number greater then 0 which fits in the length of SLA IDs (see below).
Example: If ID is 1 and the client is delegated an IPv6 prefix 2001:db8:ffff::/48, dhcp6c will combine the two values into a single IPv6 prefix, 2001:db8:ffff:1::/64, and will configure the prefix on the specified interface.
set interfaces bonding bond0 vif 10 dhcpv6-options pd 0 interface eth8 sla-id 1
Port Mirror (SPAN)
SPAN port mirroring can copy the inbound/outbound traffic of the interface to the specified interface, usually the interface can be connected to some special equipment, such as behavior control system, intrusion detection system and traffic collector, and can copy all related traffic from this port. The benefit of mirroring the traffic is that the application is isolated from the source traffic and so application processing does not affect the traffic or the system performance.
VyOS uses the mirror option to configure port mirroring. The configuration is divided into 2 different directions. Destination ports should be configured for different traffic directions.
Configure port mirroring for interface inbound traffic and copy the traffic to monitor-interface
Example: Mirror the inbound traffic of bond1 port to eth3
set interfaces bondinging bond1 mirror ingress eth3
Example
The following configuration on VyOS applies to all following 3rd party vendors. It creates a bond with two links and VLAN 10, 100 on the bonded interfaces with a per VIF IPv4 address.
# Create bonding interface bond0 with 802.3ad LACP
set interfaces bonding bond0 hash-policy 'layer2'
set interfaces bonding bond0 mode '802.3ad'
# Add the required vlans and IPv4 addresses on them
set interfaces bonding bond0 vif 10 address 192.168.0.1/24
set interfaces bonding bond0 vif 100 address 10.10.10.1/24
# Add the member interfaces to the bonding interface
set interfaces bonding bond0 member interface eth1
set interfaces bonding bond0 member interface eth2
Note
If you happen to run this in a virtual environment like by EVE-NG
you need to ensure your VyOS NIC is set to use the e1000 driver. Using the
default virtio-net-pci or the vmxnet3 driver will not work. ICMP
messages will not be properly processed. They are visible on the virtual wire
but will not make it fully up the networking stack.
You can check your NIC driver by issuing show interfaces ethernet
eth0 physical | grep -i driver
Cisco Catalyst
Assign member interfaces to PortChannel
interface GigabitEthernet1/0/23
description VyOS eth1
channel-group 1 mode active
!
interface GigabitEthernet1/0/24
description VyOS eth2
channel-group 1 mode active
!
A new interface becomes present Port-channel1, all configuration like
allowed VLAN interfaces, STP will happen here.
interface Port-channel1
description LACP Channel for VyOS
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 10,100
switchport mode trunk
spanning-tree portfast trunk
!
Juniper EX Switch
For a headstart you can use the below example on how to build a bond with two interfaces from VyOS to a Juniper EX Switch system.
# Create aggregated ethernet device with 802.3ad LACP and port speeds of 10gbit/s
set interfaces ae0 aggregated-ether-options link-speed 10g
set interfaces ae0 aggregated-ether-options lacp active
# Create layer 2 on the aggregated ethernet device with trunking for our vlans
set interfaces ae0 unit 0 family ethernet-switching port-mode trunk
# Add the required vlans to the device
set interfaces ae0 unit 0 family ethernet-switching vlan members 10
set interfaces ae0 unit 0 family ethernet-switching vlan members 100
# Add the two interfaces to the aggregated ethernet device, in this setup both
# ports are on the same switch (switch 0, module 1, port 0 and 1)
set interfaces xe-0/1/0 ether-options 802.3ad ae0
set interfaces xe-0/1/1 ether-options 802.3ad ae0
# But this can also be done with multiple switches in a stack, a virtual
# chassis on Juniper (switch 0 and switch 1, module 1, port 0 on both switches)
set interfaces xe-0/1/0 ether-options 802.3ad ae0
set interfaces xe-1/1/0 ether-options 802.3ad ae0
Aruba/HP
For a headstart you can use the below example on how to build a bond,port-channel with two interfaces from VyOS to a Aruba/HP 2510G switch.
# Create trunk with 2 member interfaces (interface 1 and 2) and LACP
trunk 1-2 Trk1 LACP
# Add the required vlans to the trunk
vlan 10 tagged Trk1
vlan 100 tagged Trk1
Arista EOS
When utilizing VyOS in an environment with Arista gear you can use this blue print as an initial setup to get an LACP bond / port-channel operational between those two devices.
Lets assume the following topology:
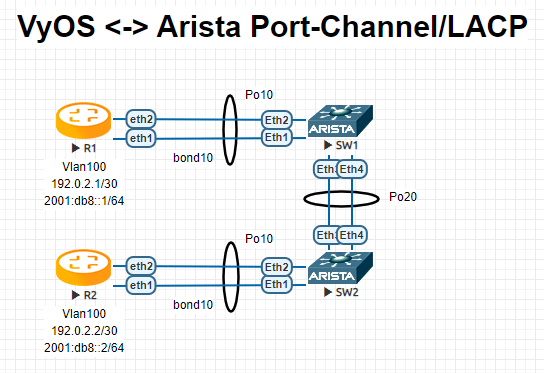
R1
interfaces { bonding bond10 { hash-policy layer3+4 member { interface eth1 interface eth2 } mode 802.3ad vif 100 { address 192.0.2.1/30 address 2001:db8::1/64 } }
R2
interfaces { bonding bond10 { hash-policy layer3+4 member { interface eth1 interface eth2 } mode 802.3ad vif 100 { address 192.0.2.2/30 address 2001:db8::2/64 } }
SW1
! vlan 100 name FOO ! interface Port-Channel10 switchport trunk allowed vlan 100 switchport mode trunk spanning-tree portfast ! interface Port-Channel20 switchport mode trunk no spanning-tree portfast auto spanning-tree portfast network ! interface Ethernet1 channel-group 10 mode active ! interface Ethernet2 channel-group 10 mode active ! interface Ethernet3 channel-group 20 mode active ! interface Ethernet4 channel-group 20 mode active !
SW2
! vlan 100 name FOO ! interface Port-Channel10 switchport trunk allowed vlan 100 switchport mode trunk spanning-tree portfast ! interface Port-Channel20 switchport mode trunk no spanning-tree portfast auto spanning-tree portfast network ! interface Ethernet1 channel-group 10 mode active ! interface Ethernet2 channel-group 10 mode active ! interface Ethernet3 channel-group 20 mode active ! interface Ethernet4 channel-group 20 mode active !
Note
When using EVE-NG to lab this environment ensure you are using e1000 as the desired driver for your VyOS network interfaces. When using the regular virtio network driver no LACP PDUs will be sent by VyOS thus the port-channel will never become active!
Operation
Show brief interface information.
vyos@vyos:~$ show interfaces bonding
Codes: S - State, L - Link, u - Up, D - Down, A - Admin Down
Interface IP Address S/L Description
--------- ---------- --- -----------
bond0 - u/u my-sw1 int 23 and 24
bond0.10 192.168.0.1/24 u/u office-net
bond0.100 10.10.10.1/24 u/u management-net
Show detailed information on given <interface>
vyos@vyos:~$ show interfaces bonding bond5
bond5: <NO-CARRIER,BROADCAST,MULTICAST,MASTER,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether 00:50:56:bf:ef:aa brd ff:ff:ff:ff:ff:ff
inet6 fe80::e862:26ff:fe72:2dac/64 scope link tentative
valid_lft forever preferred_lft forever
RX: bytes packets errors dropped overrun mcast
0 0 0 0 0 0
TX: bytes packets errors dropped carrier collisions
0 0 0 0 0 0
Show detailed information about the underlaying physical links on given bond <interface>.
vyos@vyos:~$ show interfaces bonding bond5 detail
Ethernet Channel Bonding Driver: v3.7.1 (April 27, 2011)
Bonding Mode: IEEE 802.3ad Dynamic link aggregation
Transmit Hash Policy: layer2 (0)
MII Status: down
MII Polling Interval (ms): 100
Up Delay (ms): 0
Down Delay (ms): 0
802.3ad info
LACP rate: slow
Min links: 0
Aggregator selection policy (ad_select): stable
Slave Interface: eth1
MII Status: down
Speed: Unknown
Duplex: Unknown
Link Failure Count: 0
Permanent HW addr: 00:50:56:bf:ef:aa
Slave queue ID: 0
Aggregator ID: 1
Actor Churn State: churned
Partner Churn State: churned
Actor Churned Count: 1
Partner Churned Count: 1
Slave Interface: eth2
MII Status: down
Speed: Unknown
Duplex: Unknown
Link Failure Count: 0
Permanent HW addr: 00:50:56:bf:19:26
Slave queue ID: 0
Aggregator ID: 2
Actor Churn State: churned
Partner Churn State: churned
Actor Churned Count: 1
Partner Churned Count: 1