VRF
VRF devices combined with ip rules provides the ability to create virtual routing and forwarding domains (aka VRFs, VRF-lite to be specific) in the Linux network stack. One use case is the multi-tenancy problem where each tenant has their own unique routing tables and in the very least need different default gateways.
Configuration
A VRF device is created with an associated route table. Network interfaces are then enslaved to a VRF device.
Create new VRF instance with <name>. The name is used when placing individual interfaces into the VRF.
Configure use routing table <id> used by VRF <name>.
Note
A routing table ID can not be modified once it is assigned. It can only be changed by deleting and re-adding the VRF instance.
By default the scope of the port bindings for unbound sockets is limited to the default VRF. That is, it will not be matched by packets arriving on interfaces enslaved to a VRF and processes may bind to the same port if they bind to a VRF.
TCP & UDP services running in the default VRF context (ie., not bound to any VRF device) can work across all VRF domains by enabling this option.
Interfaces
When VRFs are used it is not only mandatory to create a VRF but also the VRF itself needs to be assigned to an interface.
Routing
Note
VyOS 1.3 (equuleus) only supports VRF static routing. Dynamic routing for given VRFs was added in VyOS 1.4 (sagitta). This also came with a change in the CLI configuration which will be - of course - automatically migrated on upgrades.
Static
Static routes are manually configured routes, which, in general, cannot be updated dynamically from information VyOS learns about the network topology from other routing protocols. However, if a link fails, the router will remove routes, including static routes, from the RIPB that used this interface to reach the next hop. In general, static routes should only be used for very simple network topologies, or to override the behavior of a dynamic routing protocol for a small number of routes. The collection of all routes the router has learned from its configuration or from its dynamic routing protocols is stored in the RIB. Unicast routes are directly used to determine the forwarding table used for unicast packet forwarding.
Static Routes
Configure next-hop <address> for an IPv4 static route in the VRF identified by <name>. Multiple static routes can be created.
Disable IPv4 static route entry in the VRF identified by <name>
Defines next-hop distance for this route, routes with smaller administrative distance are elected prior those with a higher distance.
Range is 1 to 255, default is 1.
Configure next-hop <address> for an IPv6 static route in the VRF identified by <name>. Multiple IPv6 static routes can be created.
Disable IPv6 static route entry in the VRF identified by <name>.
Defines next-hop distance for this route, routes with smaller administrative distance are elected prior those with a higher distance.
Range is 1 to 255, default is 1.
Note
Routes with a distance of 255 are effectively disabled and not installed into the kernel.
Leaking
Use this command if you have shared services or routes that should be shared between multiple VRF instances. This will add an IPv4 route to VRF <name> routing table to reach a <subnet> via a next-hop gatewys <address> in a different VRF or leak it into the default VRF.
Use this command if you have shared services or routes that should be shared between multiple VRF instances. This will add an IPv6 route to VRF <name> routing table to reach a <subnet> via a next-hop gatewys <address> in a different VRF or leak it into the default VRF.
Interface Routes
Allows you to configure the next-hop interface for an interface-based IPv4 static route. <interface> will be the next-hop interface where trafic is routed for the given <subnet>.
Disables interface-based IPv4 static route.
Defines next-hop distance for this route, routes with smaller administrative distance are elected prior those with a higher distance.
Range is 1 to 255, default is 1.
Allows you to configure the next-hop interface for an interface-based IPv6 static route. <interface> will be the next-hop interface where trafic is routed for the given <subnet>.
Disables interface-based IPv6 static route.
Blackhole
Use this command to configure a “black-hole” route on the router. A black-hole route is a route for which the system silently discard packets that are matched. This prevents networks leaking out public interfaces, but it does not prevent them from being used as a more specific route inside your network.
Defines blackhole distance for this route, routes with smaller administrative distance are elected prior those with a higher distance.
Use this command to configure a “black-hole” route on the router. A black-hole route is a route for which the system silently discard packets that are matched. This prevents networks leaking out public interfaces, but it does not prevent them from being used as a more specific route inside your network.
Operation
It is not sufficient to only configure a VRF but VRFs must be maintained, too. For VRF maintenance, the following operational commands are in place.
List VRFs that have been created
vyos@vyos:~$ show vrf
VRF name state mac address flags interfaces
-------- ----- ----------- ----- ----------
blue up 00:53:12:d8:74:24 noarp,master,up,lower_up dum200,eth0.302
red up 00:53:de:02:df:aa noarp,master,up,lower_up dum100,eth0.300,bond0.100,peth0
Note
Command should probably be extended to list also the real interfaces assigned to this one VRF to get a better overview.
vyos@vyos:~$ show vrf name blue
VRF name state mac address flags interfaces
-------- ----- ----------- ----- ----------
blue up 00:53:12:d8:74:24 noarp,master,up,lower_up dum200,eth0.302
Display IPv4 routing table for VRF identified by <name>.
vyos@vyos:~$ show ip route vrf blue
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
VRF blue:
K 0.0.0.0/0 [255/8192] unreachable (ICMP unreachable), 00:00:50
S>* 172.16.0.0/16 [1/0] via 192.0.2.1, dum1, 00:00:02
C>* 192.0.2.0/24 is directly connected, dum1, 00:00:06
Display IPv6 routing table for VRF identified by <name>.
vyos@vyos:~$ show ipv6 route vrf red
Codes: K - kernel route, C - connected, S - static, R - RIPng,
O - OSPFv3, I - IS-IS, B - BGP, N - NHRP, T - Table,
v - VNC, V - VNC-Direct, A - Babel, D - SHARP, F - PBR,
f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
VRF red:
K ::/0 [255/8192] unreachable (ICMP unreachable), 00:43:20
C>* 2001:db8::/64 is directly connected, dum1, 00:02:19
C>* fe80::/64 is directly connected, dum1, 00:43:19
K>* ff00::/8 [0/256] is directly connected, dum1, 00:43:19
The ping command is used to test whether a network host is reachable or not.
Ping uses ICMP protocol’s mandatory ECHO_REQUEST datagram to elicit an ICMP ECHO_RESPONSE from a host or gateway. ECHO_REQUEST datagrams (pings) will have an IP and ICMP header, followed by “struct timeval” and an arbitrary number of pad bytes used to fill out the packet.
When doing fault isolation with ping, your should first run it on the local host, to verify that the local network interface is up and running. Then, continue with hosts and gateways further down the road towards your destination. Round-trip times and packet loss statistics are computed.
Duplicate packets are not included in the packet loss calculation, although the round-trip time of these packets is used in calculating the minimum/ average/maximum round-trip time numbers.
Ping command can be interrupted at any given time using <Ctrl>+c- A brief statistic is shown afterwards.
vyos@vyos:~$ ping 192.0.2.1 vrf red
PING 192.0.2.1 (192.0.2.1) 56(84) bytes of data.
64 bytes from 192.0.2.1: icmp_seq=1 ttl=64 time=0.070 ms
64 bytes from 192.0.2.1: icmp_seq=2 ttl=64 time=0.078 ms
^C
--- 192.0.2.1 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 4ms
rtt min/avg/max/mdev = 0.070/0.074/0.078/0.004 ms
Displays the route packets take to a network host utilizing VRF instance identified by <name>. When using the IPv4 or IPv6 option, display the route packets take to the for the given hosts IP address family. This option is useful when the host specified is a hostname rather than an IP address.
Example
VRF route leaking
The following example topology was build using EVE-NG.
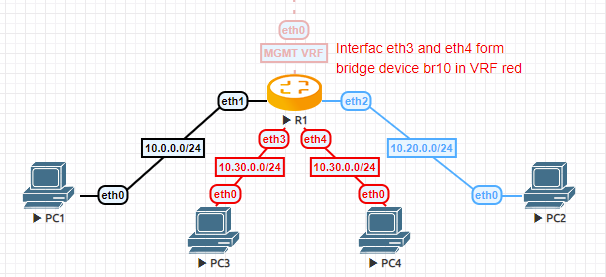
VRF route leaking
PC1 is in the
defaultVRF and acting as e.g. a “fileserver”PC2 is in VRF
bluewhich is the development departmentPC3 and PC4 are connected to a bridge device on router
R1which is in VRFred. Say this is the HR department.R1 is managed through an out-of-band network that resides in VRF
mgmt
Configuration
set interfaces bridge br10 address '10.30.0.254/24' set interfaces bridge br10 member interface eth3 set interfaces bridge br10 member interface eth4 set interfaces bridge br10 vrf 'red' set interfaces ethernet eth0 address 'dhcp' set interfaces ethernet eth0 vrf 'mgmt' set interfaces ethernet eth1 address '10.0.0.254/24' set interfaces ethernet eth2 address '10.20.0.254/24' set interfaces ethernet eth2 vrf 'blue' set protocols static interface-route 10.20.0.0/24 next-hop-interface eth2 next-hop-vrf 'blue' set protocols static interface-route 10.30.0.0/24 next-hop-interface br10 next-hop-vrf 'red' set protocols vrf blue static interface-route 10.0.0.0/24 next-hop-interface eth1 next-hop-vrf 'default' set protocols vrf red static interface-route 10.0.0.0/24 next-hop-interface eth1 next-hop-vrf 'default' set service ssh disable-host-validation set service ssh vrf 'mgmt' set system domain-name 'vyos.net' set system host-name 'R1' set system name-server 'eth0' set vrf name blue table '3000' set vrf name mgmt table '1000' set vrf name red table '2000'
Operation
After committing the configuration we can verify all leaked routes are installed, and try to ICMP ping PC1 from PC3.
PCS> ping 10.0.0.1 84 bytes from 10.0.0.1 icmp_seq=1 ttl=63 time=1.943 ms 84 bytes from 10.0.0.1 icmp_seq=2 ttl=63 time=1.618 ms 84 bytes from 10.0.0.1 icmp_seq=3 ttl=63 time=1.745 msVPCS> show ip NAME : VPCS[1] IP/MASK : 10.30.0.1/24 GATEWAY : 10.30.0.254 DNS : MAC : 00:50:79:66:68:0f
VRF default routing table
vyos@R1:~$ show ip route Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP, T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP, F - PBR, f - OpenFabric, > - selected route, * - FIB route, q - queued, r - rejected, b - backup C>* 10.0.0.0/24 is directly connected, eth1, 00:07:44 S>* 10.20.0.0/24 [1/0] is directly connected, eth2 (vrf blue), weight 1, 00:07:38 S>* 10.30.0.0/24 [1/0] is directly connected, br10 (vrf red), weight 1, 00:07:38
VRF red routing table
vyos@R1:~$ show ip route vrf red Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP, T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP, F - PBR, f - OpenFabric, > - selected route, * - FIB route, q - queued, r - rejected, b - backup VRF red: K>* 0.0.0.0/0 [255/8192] unreachable (ICMP unreachable), 00:07:57 S>* 10.0.0.0/24 [1/0] is directly connected, eth1 (vrf default), weight 1, 00:07:40 C>* 10.30.0.0/24 is directly connected, br10, 00:07:54
VRF blue routing table
vyos@R1:~$ show ip route vrf blue Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP, T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP, F - PBR, f - OpenFabric, > - selected route, * - FIB route, q - queued, r - rejected, b - backup VRF blue: K>* 0.0.0.0/0 [255/8192] unreachable (ICMP unreachable), 00:08:00 S>* 10.0.0.0/24 [1/0] is directly connected, eth1 (vrf default), weight 1, 00:07:44 C>* 10.20.0.0/24 is directly connected, eth2, 00:07:53